David Šaur
Thomas Bata University in Zlín, Faculty of Applied Informatics
Nad Stráněmi 4511, Zlín, 76001
Email: saur@fai.utb.cz
Abstract: The article discusses the use of selected information support for critical infrastructure protection, planning and recovery in the elements (companies) in extraordinary event or a crisis situation. The article describes four software tools, which are available at Faculty of Applied Informatics. Initially the first two software tools RISKAN and SFERA are given, which are very often used for risk analysis in the critical infrastructure protection. However, we can also take advantage of the risk analysis in the private sphere. Two other tools Recovery Planner RPX and ORMS Consultant are intended for planning and recovery company affected the extraordinary event and advisory activities in the assets protection. For each software tools are listed the basic information, including system requirements, characteristics of the main components and their practical use. The conclusion summarizes the elementary information about each of the software, including their advantages and disadvantages.
Keywords: information support, critical infrastructure, software, extraordinary event
1. Introduction
Information support for critical infrastructure protection is a set of information activities in supporting decision, making, management, and cognitive processes. The aim of the information support for critical infrastructure protection is to satisfy the information needs, which are necessary for the performance of activities related to the critical infrastructure protection. Other objectives of the information support is to reduce the risk of an incident or crisis situations, the mitigation of their consequences and effective security for the return of the affected area or organization in the normal (initial) state. To achieve these objectives, it is necessary to get a large amount of information that must be available at the right time and at the right place for effective crisis authorities’ decision of company. This information support should secure the collection and processing of data, including the retention of the quick search options, transmission and other use of the information. [1], [2]
Department of security engineering Faculty of Applied Informatics at Tomas Bata University in Zlín purchased five software tools for the purpose of resolving the security project MVVG20112014067 and development of a workplace for critical infrastructure resilience rating. In the context of this article is a brief description of the software tool RISKAN, which is widely used for risk analysis in critical infrastructure, as well as the private sector. The software application SFERA can also be used when assessing threats and risk analysis for state and private sector, Recovery Planning RPX in the planning and recovery resources during extraordinary event in companies and ORMS Consultant as a tool in consultancy activities to ensure the protection of corporate assets. These software tools such as SFERA, Recovery Planning RPX and ORMS Consultant have not been used in the context of teaching yet, but their use will be planned for educational purposes in the near future. Therefore, within this article we want to inform public with their use in the critical infrastructure protection, which is also enshrined in a number of projects and research activities in the Faculty of Applied Informatics.
2. Software application RISKAN
2.1. Characteristic
A software application RISKAN was created by T-Soft a.s., Prague. It is used as a support tool when compiling the semi quantitative risks analysis for all critical infrastructure sectors.
This software works in the process of risk analysis with profiles in relation to the analyzed entity. In each profile are evaluated by three basic security elements: asset, threat, and vulnerability, with the possibility to assess the vulnerability of individual assets to individual threats. The supporting base for the processing of the risk analysis represents an overview of the assets and the threats of the evaluated object, where the assets and threats of similar character can be associated into different groups. Evaluation proceeds according to a scale of values defined in advance for the assets, threats, and vulnerabilities. It makes easier to set priorities that need to be respected and facilitates calculations of risk consequences. It can be an important tool for experts who are professionally engaged of risk analysis and have enough experiences.
Excel worksheets (MS Office 2003/2007/2010) has a simple operation and is suitable for operational, rapid and local deployment. You can also use it as a server application with web interface, in addition with the function of generating data into worksheets of MS Excel.
The tool is intended for individual or team use, it does not accurate figures. It also allows customizing profiles to specific conditions to match the organization environment.
Perform a risk analysis with the use of the software RISKAN enable to speed up the whole process, prepare clear outputs and conclusions for deciding on the next steps on the part of the organization’s management and security specialists. In addition, this procedure makes it easier to repeat the analysis to change the conditions of the analyzed system or his security.
For full use of the software must have RISKAN available desktop computer or a laptop with Microsoft Windows operating system version 2003 and later versions. In terms of software requirements, you must have installed Microsoft Office 2003 and later version 2007 and 2010 to work with Microsoft Excel. [1], [3], [4]
2.2. Main components
The software tool RISKAN is situated in the MS Excel worksheets:
I. Help sheet – includes basic information about using the tool RISKAN.
II. Figure sheet - contains figures the probability of asset values, threats and vulnerabilities. These figures are governed by specifying values on the worksheets in the Assets value (0-5), Threats (probabilities 0-5) and the Vulnerability of assets value (0-5), and the Resulting risk.
III. Data sheet - is used for the display of the values risks, at the same time shows the value assets and the probability of threats that you entered on the lists of Assets and Threats. For the quantification of the resulting risks are also applied to the value vulnerability that you entered on the worksheet, Vulnerability. Sheets the threats and assets are organized into groups, with the line or column group is grayed out something. To display and hide the contents of the groups used the controls to collapse and expand the groups, levels see figure above (red marked). To display the resulting risks on the worksheet on the list Data is necessary to specify the value assets on the Assets worksheet, the threat probabilities on a Threat worksheet and the values vulnerability on the Vulnerability worksheet. Then the resulting values are displayed on the worksheet Data.
Cells on the Data worksheet is marked according to the resulting values (see figure below):
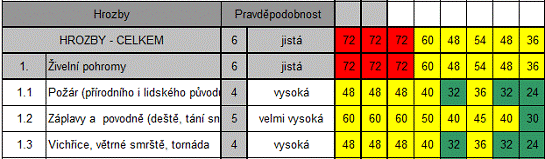
Fig. 1: RISKAN - Data Sheet [5]
IV. Vulnerability sheet - used to enter vulnerabilities. To display and hide the groups contents used the controls to collapse and expand the group levels (see the image above – in red marked). Vulnerability values are entered to the blue cells. If you specify value vulnerability outside the values range allowed in the figure, it is displayed error message. You can insert the value vulnerability in the line with the main group (then this value will overwrite all the rows in the partial group) or to the row group (then in the main group of partial fills in the lines). It is the same as for inserting values into columns.
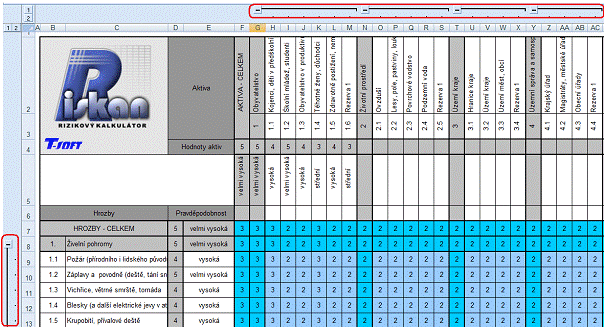
Fig. 2: Sheet vulnerability [5]
V. Assets sheet - Assets are organized into groups. These groups can be understood as the individual critical infrastructure sectors for example energy, transport, information and communication technologies, postal services, public administration and health care. You can click on a special control (pictured below in red marked) to show or hide the assets in the group. For each asset in the group must be filled on the Assets worksheet his values; the software tool automatically retrieves the text description of the height values on the Data and Vulnerability sheets. The value assets and the descriptive texts are on the Dials list. The value of group assets (line group is colored in grey) is specified as the maximum value of individual assets from the group – to insert the values into line with individual assets (cell to insert values is colored in blue). But if you enter a value in the row groups of assets (the line is grayed out something), it will overwrite this value in all individual assets in the group.
VI. Threats sheet - Threats are organized into two basic groups of natural extraordinary events (negative phenomena caused by the weather, earthquakes, epidemics, etc.) and anthropogenic extraordinary events (supply disruption, technological and functional crash, migration waves, etc.). You can click on a special control (pictured below in red marked) to show or hide the threat in a group. You must complete the worksheet on the threat value of the probability of its application for each threat; the tool automatically retrieves the text description of the values on the Data and Vulnerability sheets. The value of the group threats (the row with the group is colored in grey) is specified as the maximum value of each threats from the group to insert the values into line with the individual threats (cells for inserting values are blue). But if you enter a value in the row groups threats (the line is grayed out something), it will overwrite the value of the individual threats in the group.
The process of risk analysis in the calculator RISKAN includes:
1) The identification of assets and their evaluation (evaluation scale of 0-5):
2) Identification of the threats and assess their probabilities (evaluation scale of 0-5):
3) Assess the vulnerabilities of assets each threats (evaluation scale of 0-5):
4) The calculation of the resulting risks for each relevant pair of asset-threat:
![]()
5) Sorting the resulting risks on "low, medium and high" according to specified criteria. [5]
2.3. Practical use
Example the tool RISKAN use will be briefly described in practice in this chapter. Software RISKAN is used in combination with some other software tools in many case studies. In this example, it will be about a leak of ammonia, where the second tool in combination with the RISKAN is software TerEx[1]. Through the program RISKAN are established asset values, threats and vulnerabilities to assets. The result will be the calculation of the risks for the population, components of the integrated rescue system and cultural facilities.
The threat is the danger of intoxication with ammonia in this case. Highly vulnerable assets are winter stadium Luďka Čajky and PSG arena. Medium-sized endangered assets are sports hall Novesta and guesthouse Koliba. Assets at risk low risk are unimportant. When calculating the risk the status of before and after the reconstruction of the stadium was examined. It was higher before reconstruction. In the current state, it was a high risk population (mainly adults) and guesthouse Koliba. A threat to the prospect of the nursery school and the headquarters of the Police of the Czech Republic can be considered for medium risk. Other risks have been evaluated as insignificant. It is essential to note that the program RISKAN uses to analyze risks semi-quantitative approach. [4]
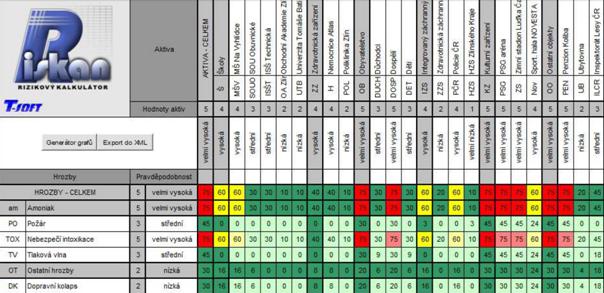
Fig. 3: The result of the calculation of risks in the risk calculator RISKAN [4]
3. SFERA
3.1. Characteristic
The software application SFERA (System Phenomena Effect Risk Analysis) was created by the company BOBYsoft a.s. specifically for the risk analysis of emergency territorial and objects plans. This software application has been developed and tested by crisis managers on the model examples since 1996.
The software application SFERA intellectually builds on the well known analytical methods in order to zoom in as far as possible the philosophy thinking of crisis managers when considering possible threats in the system. Emphasis is placed on speed and simplicity of work on the one hand, and the clarity and brevity of the outputs interpretation on the other side. For granted is considered as teamwork and the possibility of outputs verification with other analytical methods. The software application SFERA is explicitly designed for analytical purposes, but it can be useful for a quick multi-objective decision-making when the manager does not work with probabilities and plenty of risks.
The software application SFERA differs for its ability to solve the problems of invisible circularity in the parsed structure unlike from similar systems. In principle, the program allows you to create contingency tables, where through mathematical operations defined in the context of the data classified under the diagonal. In addition to the formal data editing and their registration in the database of analytical findings, design and processing criteria in the value calculation, the vulnerabilities calculation of individual risks with regard to time parameters, export calculated data from MS Excel, HTML pages, or to MS Word, including the display of the results into the tree or guidance chart development.
For work with the software application SFERA, you must have a desktop computer or laptop with Windows operating systems with versions by the year 2011, CD rack with the software installation (install on HDD size 7, 5 MB) and HASP USB key without which it would not be possible to start the program SFERA. [1]
3.2. The main components
The program SFERA is divided into five separate parts (windows), which are linked in a sequence when you create a workflow analysis.
The windows are designed for the following functions:
1. A window with the name "The Matrix" is intended for creating a contingency table, either directly or by using a wizard. A contingency table report can be saved to a file, MS Office Excel.
2. A window with the name "Relationships" is intended for the display of the instantaneous links between individual elements in the contingency table.
3. A window with the name "Wizard to specify data" is intended for editing the threat names in the contingency table for clearing unwanted threats. From this window, you can run the file with the information about a specific element, set up the criteria parameters for the threats evaluation.
4. A window with the name "The values of the elements" is intended for specifying additional parameters to each elements before the final calculation. Data with this window and the submenu can save to the file MS Office Excel.
5. A window with the name "Results" is intended for display output in graphic form or in the influence tree. [6]
3.3. Practical use
A practical example the software application SFERA will be demonstrated on the UTB example, where the sample is analyzed the threat of "Disruption of electricity supply". In the list of the threats mentioned a total of eight threats. The vulnerability criteria are the Life, Health, Economic and Psychological casualties.
In the threats matrix is displayed with the individual threats to the contingency table, where some threats makes other threats emergence (in the matrix expressed the one value). In the element values are displayed in two tables. The first table lists the input values and the derived probabilities, casualties, the new risk probability, the relative value order and influence in % on the fixed coefficient basis of 0.1 for the value of 500 for each threat. The individual losses (Life, Health, Economic, and Psychological casualties are calculated in the second table). The percentage value the weights sum must be one hundred percent are distributed on the basis of individual criteria in line HDSA percentage. Values belong to a specific threat in line percentage casualties HDSA. Then we will evaluate and right at the bottom of the second table shows the result for a given threat. The results are displayed in the graphs and trees form calculated in tables in the elements values. On the choice we have calculated the probability charts, final order, influence and impact percentage. The chart shows that the greatest impact during the power outage will have on the economy and human health from a psychological view point. The chart is informational only, but for the analysis purpose is used in particular table exported to Excel. The tree impact is set into three levels.
Analysis is relatively quick and easy to navigate in terms of outputs due to the size of the analyzed data. The outputs interpretation is possible on the basis of the calculated data. One of the most common indicators to compare the influence values in percentage for each calculated risks. [6]
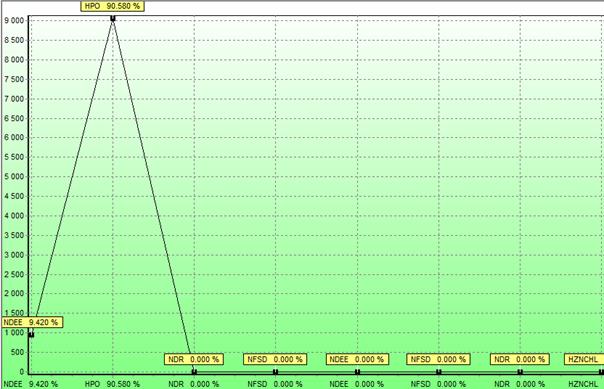
Fig. 4: The Program SFERA – the chart impact expressed in percentage
4. The Recovery Planner RPX
4.1. Characteristic
The Recovery Planner (RPX) is integrated web software from RecoveryPlanner.com, Inc. for the planning and reconstruction of the extraordinary events. RPX is a leading provider of services related to ensure the business continuity, the risk management and incidents in the company.
RPX incorporates these components of Business Continuity Management:
RPX is a tool for creating, editing and activation plans in the business. This software allows you to interactively manage and coordinate the activities necessary for the plan when the emergence of extraordinary events. RPX uses all the possibilities of the Internet, in order to meet the high demands on the business sector. It brings the largest return on investment concurrently; reduce risk, speed implementation, and regenerative processes. RPX allows you to import the results into MS Excel and Word.
For work with Web software RPX is necessary to have a desktop computer or laptop with Windows operating systems, where the current Web browsers are installed, the Microsoft Office suite (especially Excel and MS Office Word 2003 and later versions). [7]
4.2. The main components
4.3. Practical use
RPX Recovery Planner is used to planning and reconstruction in companies of the natural or anthropogenic type extraordinary events. We do analysis and risk assessment, which operates on the assets in our business before the emergence of any extraordinary events.
At first we set the values for the specified risk factors (Rf):
The overall risk (OR) is calculated as:
![]()
In this section, you can also work with three risk templates:
In the second step is performed Business Impact Analysis (BIA), where we can upload the individual functions by category, BIA lists with the BIA tables and settings. We can track the time and financial impacts and determination of total impacts in the BIA. We can watch the entire course of analysis and planning through the dashboard in the Analysis&Reporting, a list of current notifications and alerts, list of work teams, panels with topics and discussions, bookmarks and more folders (help, knowledge base, RPX forum and online training).
The second step will consist in the planning and management processes. We have to choose from a plan lists in the Project and Plan management, for example plans for the site on the Web, the Department plans, resource plans (hardware and software), the plans according to the categories and lists of working teams. Individual incidents can be set according to the incident type (a disaster event, failure, test), add logging tags incident (landmark, problem, issue, ungroup messages) and the type of result (failures, password). We choose lists or notification messages in the alert settings, which are used in the context of incidents. We have a choice of three notification types (department, resources and site news). We have many templates to choose from concerning the ISO standards in the Compliance section, laws and guidelines for planning and restoration of the undertaking in the incident.
The third step is carried out by managing critical resources. First, we enter into the system of assets where may set the individual parameters for relationships, phase, statistics, navigation, configuration, etc. In the section the Relationships are displayed to their lists, including all of the relevant contracts. In the section Integration we can see a list of staff with information about every person working in the company. In the last section of the Files we can upload any files relating to the planning and recovery of the enterprise.
In the fourth step we can watch communications between individuals, suppliers, customers, which refers to the section of the incidents. It is also possible to follow through all the geographic information system.
The work output while browsing these sections is to create the final reports of all sources, threats, risks, warnings, summarized in the different plan types for the prevention, preparation, planning and reconstruction after the creation of any type extraordinary event.
5. ORMS Consultant
5.1. Characteristics
ORMS Consultant from the company Outsourced Risk Management Solutions LLC is the software suitable for consulting firms or individual consultants and advisors, who are responsible for the care of the resilience requirements in multiple client organizations. It is suitable for most clients of industrial and production categories, all business sectors, state and federal agencies. This software is focused on consultation with organizations that want to implement best practices for the preparation and protection from potentially dangerous incidents, improve the level of client resilience measurement, ensure compliance and generally strengthen the activities in corporate governance.
ORMS Consultant provides a variety of tools, advice and techniques that enable the organization to carry out organizational concepts of resilience. ORMS Consultant is a relational database management system, which is intended to help users in the implementation and achieve compliance with the standard ASIS SPC. 1-2009.This is the American national standard for improving the organization resilience, which includes these following components:
· security,
· preparedness,
· the continuity and
· the management system
ORMS Consultant contains the complete text of the OR standard and requirements on the interactive format. This standard incorporates the procedural approach to the development, implementation, and operation, monitoring, maintaining and improving the flexibility of the organization. It is based on the Plan-Do-Check-Act (PDCA) model. ORMS Consultant is able to support multiple data files. The user has the opportunity to identify the deficiencies in the level of compliance and to support the development of appropriate processes and procedures.
ORMS Consultant also supports the development of effective organizational resilience management system delivering a very wide range of functions mapping all operating elements, risks analysis and impacts on the business, planning, response and continuity, the deployment of responsible persons, assets and resource planning.
For working with web-based software ORMS Consultant you need to have a desktop computer or laptop with Windows operating systems, including current Web browsers. [8]
5.2. The main components and practical use
In the first stage it is necessary to ensure that all the processes are carried out according to the standards and the organization ensures the implementation and organizational flexibility to improve safety, preparedness, response, recovery and continuity. At first, the organization should establish the critical assets and potential risk scenarios in case of extraordinary event. The review should include the risks identification associated with operating conditions, the requirements identification for the specific legislation, an assessment of the existing risk management practices, and evaluation of previous emergency situations.
In the second stage it is necessary to ensure security policy for compliance with the applicable legislation, to ensure the prevention, preparedness and mitigation of incidents, including the process of continuous improvement.
The third phase includes the planning process, the risks identification, threats and impacts, where it is necessary to ensure in particular, those which are important and should be addressed as a priority. Critical activities, functions, and processes should be identified and documented (purchasing, production, supply, sale, distribution, etc.). Subsequently, comprehensive risks analysis and impacts is realized within the management system. In the framework of risk analysis is to examine the particular risks associated with enterprise features, products and services; mutual dependence; the risks associated with cyber security, etc. In the impact assessment it is necessary to take into account the human, financial, environmental impacts and economic losses to the organization.
The fourth phase consists the implementation of the operation where lays down resources, tasks, responsibilities and obligations of all parties to the organization. The organization must establish the appropriate management team to cope with the crisis and incidents. In the framework of crisis management must be handled by the emergency plans for dealing with potential crises. Then it must be carried out on regular and personnel training for increasing safety awareness. Within an organization, it is important to have secure communications and warnings in the form of information systems, bulletin boards, newsletters and websites. Furthermore, documentation must be provided a description of the management system and their control (security policy, information about risks, internal and external standards, contingency and emergency plans, records, etc.). In the implementation process is the responsibility of each organization to develop accident prevention, preparedness and response to the emergence of extraordinary events (warning signs, precursors, etc.).
The fifth (last) phase is finished with the final control, which consists in monitoring and measuring of knowledge to identify significant risks and impacts, compliance assessment with the legislation, the staff use and testing scenarios to clarify the identification of deficiencies, disagreements and incidents (corrective action and preventive measures), internal audit (examination management system, assessment of risks and impacts, regulatory requirements).
ORMS Consultant includes all these stages, which each organization should gradually go through. This process objective should be continuous improvement and cyclic repetition of all these phases. It is not a closed circle, but rather a continuous cycle in process improvement and maintenance management system. [9]
6. Conclusion
This article is about the selected software tools which can be used for the critical infrastructure protection. For businesses can serve as a basic source of information for the study and educational purposes in the future, not only for students and teachers, but also for the public dealing with this issue. In this article context, basic information were summarized about four software instruments purchased by the Tomas Bata University in Zlín in the framework of the project VG20112014067 intended for research in the security areas. The first software tool was designed for risk analysis RISKAN with semi quantitative access. RISKAN runs in MS Excel and offers a wide selection from each areas of critical infrastructure, threats, and other parameters. The output is the determination of the overall risk values for the assets, threats, and vulnerabilities. All information is recorded in graphs.
The second software application SFERA, where it once again sets the parameters for each threat and vulnerability, on the basis of the overall risk is calculated. The outputs can be expressed in graphs or the tree structure. This program is also used for the risks analysis in the public and private sphere.
The third software tool is the Recovery Planner RPX designed for planning and reconstruction of emergencies caused by natural influences or human activities. It is designed exclusively for risk analysis on the basis of assets within the company. Outside of the plans allows incidents monitoring within the company, visualization through a geographic information system, etc.
The last tool is ORMS Consultant designed for consulting activities for management. It allows monitoring of incidents within the company and works on a similar basis as Recovery Planner (collection of information about the assets, threats, evaluating impacts, making plans and final rights).
For the illustrative summary of the advantages and disadvantages of individual software tools is given below in table 1:
|
Software tools |
The Benefits Of |
The Disadvantages Of |
|
RISKAN |
· Intended for professional workers in risk analysis · To better facilitate the priorities setting and the calculation of the risk severity · Work in MS Excel – operational, rapid and local deployment · Can be used as a server application with a Web interface · Team use, does not require precise figures, · Acceleration of the processes, outputs and conclusions |
· Expertise · Professional creativity |
|
SFERA |
· The work speed and simplicity with the program · The clarity and brevity of the outputs interpretation · Team work and output verification with other instruments · Invisible circular relationships inside the parsed structure · A fast multi-objective decision-making · Export to MS Excel and Word, HTML pages |
· Designed explicitly for analytical purposes · The software on the USB HASP key (program SFERA cannot run without this key) |
|
RPX Recovery Planner |
· Ensure business continuity, risk management, and incidents in the company · Creating, editing and activation plans · Interactive management and activities coordination · The use of all the possibilities of the Internet to meet the high demands · The greatest return on investment, reduce risk, speed implementation, and regenerative processes · Import the results into MS Excel and Word |
· Actual Web browser, · Windows operating systems |
|
ORMS Consultant |
· Intended not only for businesses, but also for public administration · Implementation of best practices, regulations and standards · Protection against potentially dangerous incidents · Improving the level of client resistance · A wide range of functions mapping all elements, risk analysis and impact assessment, asset and resource planning · Support for multiple data formats |
· Actual Web browsers · Windows operating systems |
Table1: Advantages and disadvantages of information support for critical infrastructure protection
7. References
[1] DROZDEK, Marek a Katarína JELŠOVSKÁ. SLEZSKÁ UNIVERZITA V OPAVĚ.Information
support of crisis management [online]. Opava, 2013 [cit. 2014-03-10].
[2] Information
support of crisis management | T-SOFT a.s. - information systems, security, crisis
management. T-SOFT A.S. [online]. [cit. 2014-03-10]. Dostupné z:
https://www.tsoft.cz/informacni-podpora-krizoveho-rizeni
[3] RISKAN | T-SOFT a.s. - information systems, security, crisis management. T-SOFT
A.S. [online]. 2012 [cit. 2014-03-10].
[4] Evaluation of the accident impact
when release of ammonia from the winter stadium in Zlin [online]. Zlín, 2013 [cit.
2014-03-10]. Dostupné z:
http://dspace.k.utb.cz/bitstream/handle/10563/24991/han%C3%A1k_2013_bp.pdf?sequence=1
[5]T-SOFT A.S.RISKAN – User GuideT-Soft Prague.Prague, 2012.
[6]KOVAŘÍK, František.
BOBYSOFT A.S.User guide to the program SFERA. Prague, 2012.
[7]RECOVERYPLANNER.COM.RecoveryPlanner®
Integrated Enterprise Continuity Management Software[online]. [cit. 2014-03-10].
[8] Organizational Resilience Management Software Consultant. ASIS INTERNATIONAL.
[online]. [cit. 2014-03-10]. Dostupné z:
http://organizational-resilience.com/OrganizationResilienceConsultant.htm
[9] ASIS INTERNATIONAL.Organizational Resilience:Security, Preparedness,and Continuity
Management Systems: Requirements with Guidance for Use[online]. 2009 [cit. 2014-03-10].
Aktuální číslo
Odborný vědecký časopis Trilobit | © 2009 - 2026 Fakulta aplikované informatiky UTB ve Zlíně | ISSN 1804-1795