Inteligent Building Technologies as an important aspect of Critical Infrastructure Protection
Martin Hromada
Department of Security Engineering
Faculty of Applied Informatics, Tomas Bata Univerzity in Zlín
e-mail:hromada@fai.utb.cz
Abstract:
The present state of critical infrastructure protection is represented by elaboration of legislative tools and relevant documents actualization. Due this fact there are no requirements for technological aspects of critical infrastructure protection. This article discuss about the method which use intelligent building technologies for critical infrastructure protection optimalization in relation to integration of technological protection hardware together with building administration system. The method defines security system requirements and structure for each security level.
Key words: Intelligent Building Technologies, Critical Infrastructure, Security system, Mechanical security systems, Physical and Schedule security, Electronic security systems,
Intelligent buildings and critical infrastructure
The intelligent buildings are complex systems which integrate the technological devices management and power engineering, regulation and measure systems, week current systems and security systems and systems for transport and manipulation. The integration management creation provides good conditions for intelligent buildings systems cooperation in order to higher comfort, security, energy and administration costs saving or for the control simplification[1].
Current security risks have created necessity to define critical infrastructure as such infrastructure, which is strategically important for the state function and the loss of which has negative impacts on human lives and on the economical a social consequences for aspects of society and inhabitants. The sector of the critical infrastructure is a complex of critical infrastructure components defined in common signs. This common signs can be understand as criteria which are important for critical infrastructure component identification and designation. The Guidelines for the application of the Directive on the identification and designation of European Critical Infrastructure and the assessment of the need to improve their protection divide these criteria to three groups:
The casualties criteria — potential number of fatalities and injuries in Member State, associated with loss of service of a given infrastructure, which is above determined threshold. An injured person is defined by this document as person requiring more than 24 hours of hospitalisation.
The economic effect criteria — potential economic loss or loss of production services and goods, which are also defined as investments for temporary or additional solutions, environmental impacts and investments for sector reconstruction,
The public effect criteria — potential number of affected occupants considered by physical suffering, impact on public confidence and disruption of daily life which are characterized by number of impacted people, severity of the impact and duration of the impact[2].
Critical infrastructure sectors in Slovakia by this document are — water, food, health care, energy, nuclear energy, electronic communication, transport, industry, finance, postal services and cyber space. The critical infrastructure components are organizations, institutions, objects, services or information systems in designated critical infrastructure sector, which are strategically important for securing the basic sector or sectors functions. The critical infrastructure component identification and designation will be based on cross — cutting criteria which will be defined for each critical infrastructure sector on national level [3]. The main tasks and processes for critical infrastructure protection are:
The owner/operator obligation and field of activities will be in relation to operator security plan, which includes:
The critical infrastructure component owners/operators should use the best available techniques for present system modernization or for new system designation and this is the framework for intelligent buildings systems usage, which provides more effective energy utilization, reduce management costs or simplify the process control in building.
The critical infrastructure component security system requirements and structure for each security level
The weak current and security systems are integrate part of intelligent buildings systems and they are important components in relation to critical infrastructure component protection. This part discusses about the integration of technical protection parts to building management system for protection optimalization. The complex security needs the usage of weak current and security systems, mechanical security systems, physical and schedule security. The critical infrastructure component importance and the demand for their protection are not constant. The solution of this problem is definition of the security levels and the minimal security system requirements quantification.
The data collecting and data analyze was used for constructing the security system for each security level of critical infrastructure protection. The security system was based on national security authority notice which was established for physical security and subject security in relation to security information protection [4]. The security system was divided into four parts — mechanical security systems, electronic security systems and physical and schedule security. Each part was divided into perimeter protection, subject skin protection and point protection (figure 1).
The security level of security system was considered on the basis of security level which was characteristic for each security system component. Than the security level of security system component was transferred to the numeric value. Total value of security system was represented with summary of mechanical security systems, electronic security systems and physical and schedule security value. Than the minimal value of the security system for each security level was assessed (equation 1).
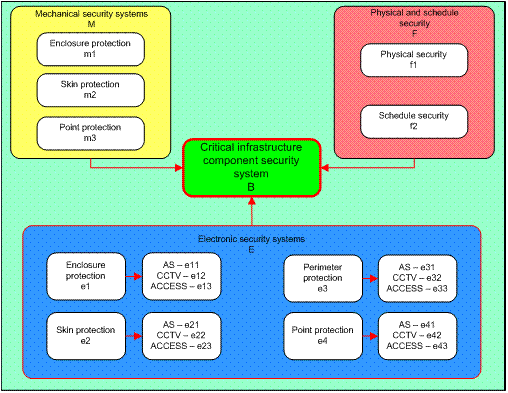
Figure 1: Security system structure
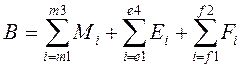
Equation 1: the value of the security system for each security level
Where:
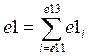 ;
;
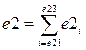 ;
;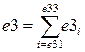 ;
;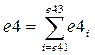
B - Numeric value of security system
M - Numeric value of mechanical security systems
m1 - Numeric value of mechanical security systems of enclosure protection
m2 - Numeric value of mechanical security systems of skin protection
m3 - Numeric value of mechanical security systems of point protection
E - Numeric value of electronic security systems
e1 - Numeric value of electronic security systems of enclosure protection for e11-e13
e2 - Numeric value of electronic security systems of skin protection for e21-e23
e3 - Numeric value of electronic security systems of perimeter protection for e31-e33
e4 - Numeric value of electronic security systems of enclosure protection for e41-e43
F - Numeric value of physical and schedule protection
f1 - Numeric value of physical protection
f2 - Numeric value of schedule protection
The minimal numeric value of security system for each security level
|
Minimal value of MSS M |
Minimal value of ESS E |
Minimal value of PS and SS P |
Minimal value of SS S |
Security level |
|
10 |
40 |
6 |
56 |
IV |
|
7 |
28 |
5 |
40 |
III |
|
4 |
16 |
4 |
24 |
II |
|
1 |
8 |
1 |
10 |
I |
Table 1: minimal numeric value of security system for each security level
The total value of the security system - S was represented with the value of sums of the mechanical security systems — M, electronic security systems — E, physical and schedule security — P. The minimal value of security system for each security level was expressed by the sum of each security system component, whereas the component values must not decrease under minimal value which was determined from the following tables.
The value of mechanical security systems — M was qualified with the values m1-m3. The m1-m3 values referenced the average value of mechanical security system components for each security level in agreement with STN P ENV1627, STN P ENV1628, STN P ENV1629, STN P ENV1630, STN EN 356 (70 0595), STN 74 7731, STN EN 1303 (16 5191), STN EN 1906 (16 5192), STN 16 5190, STN 16 5772, STN EN 12320 (16 6240), STN 96 7701, STN 96 7703. The next table showed the minimal value of mechanical security system components for each security level.
|
MSS Value m1 |
MSS Value m2 |
MSS Value m3 |
Minimal MSS Value M |
Security level |
|
3 |
4 |
3 |
10 |
IV |
|
2 |
3 |
2 |
7 |
III |
|
1 |
2 |
1 |
4 |
II |
|
0 |
1 |
1 |
2 |
I |
Table 2: minimal numeric value of mechanical security systems for each security level
The value of electronic security systems — E was the sum of values e1-e4, which presented the average sum of values of security system components. The electronic security system component structure and properties for each security level was agreed with STN EN 50133-1, STN EN 50133-2-1, STN EN 50133-7, STN EN 50131-1, STN EN 50131-1 change Z1, STN EN 50131-6, STN 33 4590-1, STN 33 4590-2, STN 33 4590-3, STN 33 4590-4, STN 33 4590-5, STN 33 4590-6, STN 33 4590-7, STN 33 4590-8, STN EN 50132-2-1, STN EN 50132-4-1, STN EN 50132-5, STN EN 50132-7. The next table pointed to the minimal value of electronic security system components for each security level.
|
ESS Value e1 |
ESS Value e2 |
ESS Value e3 |
ESS Value e4 |
Minimal ESS Value E |
Security level |
||||
|
e11 — 4 |
10 |
e21 — 4 |
10 |
e31 — 4 |
10 |
e41 — 4 |
10 |
40 |
IV |
|
e12 — 3 |
e22 — 3 |
e32 — 3 |
e42 — 3 |
||||||
|
e13 — 3 |
e23 — 3 |
e33 — 3 |
e43 — 3 |
||||||
|
e11 — 3 |
7 |
e21 — 3 |
7 |
e31 — 3 |
7 |
e41 — 3 |
7 |
28 |
III |
|
e12 — 2 |
e22 — 2 |
e32 — 2 |
e42 — 2 |
||||||
|
e13 — 2 |
e23 — 2 |
e33 — 2 |
e43 — 2 |
||||||
|
e11 — 2 |
4 |
e21 — 2 |
4 |
e31 — 2 |
4 |
e41 — 2 |
4 |
16 |
II |
|
e12 — 1 |
e22 — 1 |
e32 — 1 |
e42 — 1 |
||||||
|
e13 — 1 |
e23 — 1 |
e33 — 1 |
e43 — 1 |
||||||
|
e11 — 1 |
2 |
e21 — 1 |
2 |
e31 — 1 |
2 |
e41 — 1 |
2 |
8 |
I |
|
e12 — 1 |
e22 — 1 |
e32 — 1 |
e42 — 1 |
||||||
|
e13 — 0 |
e23 — 0 |
e33 — 0 |
e43 — 0 |
||||||
Table 3: minimal numeric value of electronic security systems for each security level
The value of physical and schedule security — P was represented with the value of sums of the f1 and f2, whereas the f1 marked the value of the physical security and f2 marked the value of the schedule security in agreement with national security department notice no. 336/2004; 315/2006, where f2 was defined with two values 0, 1decimal point). This expressed visit regime — with or without an attendant. The next table showed the minimal value of physical and schedule security — P for each security level.
|
f1 Value |
f2 Value |
Minimal P Value |
Security level |
|
5 |
1 |
6 |
IV |
|
4 |
1 |
5 |
III |
|
3 |
1 |
4 |
II |
|
2 |
0 |
2 |
I |
Table 4 minimal numeric value of physical and schedule security systems for each security level
Conclusion
This article presents the method how to determine the basic requirements a structure of critical infrastructure component security system for each security level. The critical infrastructure protection is a complex problem so the determination of concrete and relevant security system requirements and structure need wider security research. Important part of the research will be the owners/operators comments and evaluations which are essential for requirements and structure completion. The most significant aspect which affects the critical infrastructure protection level is the open communication and cooperation of state and private sector and the European funds application.
Reference
1. Shneider Electric Slovakia s.r.o., Riešenia pre inteligentné budovy, dostupné on-line: http://www.schneider-electric.sk/html_sk/riesenia/ibudovy.asp
2. Guidelines for the application of the Directive on the identification and designation of European Critical Infrastructure and the assessment of the need to improve their protection, Council of the European union, Brussels, 2008, 14808/08
3. Ministerstvo vnútra Slovenskej republiky, Návrh zákona o ochrane kritickej infraštruktúry, dostupné on-line: http://www.minv.sk/?navrh-zakona-o-ochrane-kritickej-infrastruktury
4. Vyhláška Národného bezpečnostného úradu 336/2004 Z.z. o fyzickej bezpečnosti, dostupné on-line: http://okrobukn.wbl.sk/Vyhlaska_NBU_c._336_2004_Z.z._o_ fyz.bezp..pdf
5. Smernica rady 2008/114/ES o identifikácii a označení európskych kritických infraštruktúr a zhodnotení potreby zlepšiť ich ochranu, dostupné on-line http://eur-lex.europa.eu/LexUriServ/LexUriServ.do?uri=OJ:L:2008:345:0075:0082:SK:PDF
6. HROMADA, M., Implementácia technológií inteligentných budov do problematiky ochrany kritickej infraštruktúry/ Inteligent Building Technologies Implementation to Critical Infrastructure Protection , Vliv technológií inteligentních budov na zajištění bezpečnosti objektů, Praha, 2009,
Aktuální číslo
Odborný vědecký časopis Trilobit | © 2009 - 2024 Fakulta aplikované informatiky UTB ve Zlíně | ISSN 1804-1795